WE WILL HELP YOU MOVING ON THAT YOU HAVE NEVER EXPERIENCED
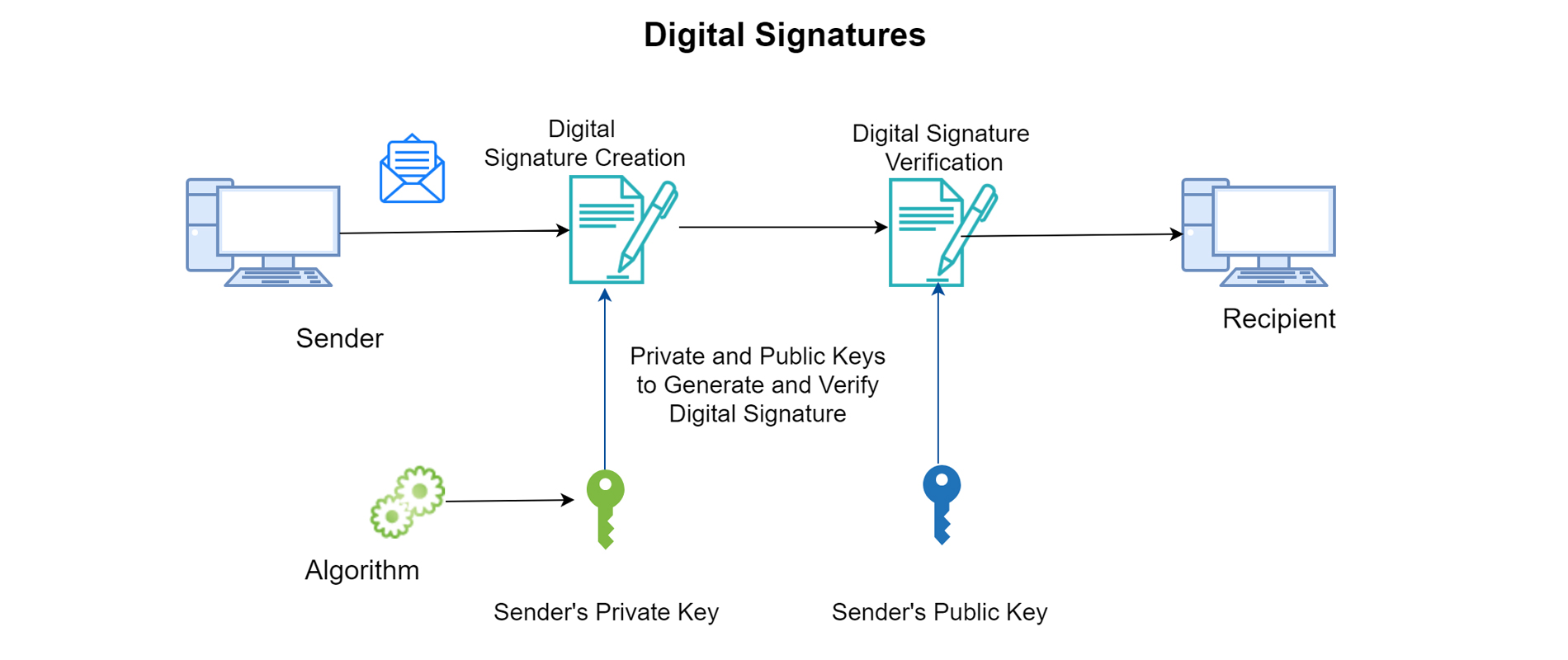
Bintel Corporaiton is a system integrator of Enterprise PKI solution. We build Enterprise Root and Sub-CA PKI including various publication schema such as LDAP, OCSP or CRL. Our PKI is built on the core community suit application of EJBCA or Dogtag or Microsoft ADCS. We also deliver and built integration on HSM on Safenet Luna or Thales ecosystem.
CLIENT CHALLENGES
- High operational costs due to the high cost of maintenance of the systems and the associated hardware
- Adherence to compliance issues and high compliance costs
- Establishment of adequate measures to ensure the protection and easy retrieval of documents
- Confusion created by the intensive competition and constant price war among CAs
Our enterprise PKI (EPKI) is a cloud-based managed PKI service to issue and manage your enterprise Client Certificates. The Enterprise PKI web portal / APIs provide administrators with a cost effective and easy to use solution to simplify PKI deployments and can built and host your own Certificate Authority. With Enterprise PKI, enterprises have the necessary tools to maintain full control of their PKI requirements without the complexities and overhead cost of running multiple physical servers. The system can be dimensioned as low as 2 physical servers with multiple virtual appliances.
Full certificate lifecycle management- issuance, renewal, free reissuance and revocation at your finger tips.
Lower costs and simplify deployment of Digital Certificates by leveraging bulk uploads, APIs and Active Directory integration to avoid manual certificate registration and installation
Scale to your needs- support multiple business units/applications with role based permissions and robust reporting, including customization and LDIF generation.
MULTI-FUNCTIONAL DIGITAL CERTIFICATES
EPKI supports delivery of client certificates for both end user and device certificate requirements, enabling PKI across a range of applications allowing organizations to:
Digitally Sign and encrypt email
Authenticate users to specific web application
Microsoft smart card login
Authorized VPN user connect with token
PKI SERVICE PORTFOLIO
BC PKI Solutions provides a number of consulting and training engagements to meet your organizational needs. These can be combined and customized to meet your specific project goals. Let us know your needs and we will work with you to scope the engagement to meet your needs. You can contact at contact@bintel.com.bd or refer to our Contact Us page.
Every project and every organization is different so there is no predefined PKI cookbook we can follow. We work with you to understand your security needs, challenges and skill set and determine how to get you to the right place. Whether you have an existing Scope-of-Work defined or are just getting started and need help defining the project, we can help.
PKI DESIGN AND IMPLEMENTATION
The proper design and architecture of a PKI is critical to its long term viability and integrity. The choices and procedures used before the first piece of software is ever installed is critical. Many security requirements must be properly defined well before the project moves forward. We can provide you the expertise you need to ensure your environment will not only meet your needs today, but is properly designed for your needs down the road.
PKI Solutions can work with you to define an environment that mitigates unacceptable security risks. We can help with that. Non-Repudiation needs? Yes, we can show you how to architect your PKI to meet those needs.
Do you need a Hardware Security Module (HSM) for your PKI Environment? Don’t know? To get the most benefit of these devices, they should be implemented before you deploy your first CA.
HARDWARE SECURITY MODULES (HSM)
Hardware Security Modules (HSM) are available from a number of manufacturers and are leveraged in a PKI to enforce defined procedures. HSMs can be used to ensure no one person can compromise a PKI. They can also be used to speed up signing/issuance in high-volume environments. HSMs can also be used to secure your CAs against the extraction and misuse of your CA private keys.
The proper selection, architecture and implementation of one or more HSMs in your environment is critical. Does your environment require a collusion requirement? If so, a K of N implementation on the HSM is recommended. Do you need to ensure a chain of custody for non-repudiation? Then the design and day-to-day history of the PKI needs to be carefully tracked and audit. This must be in place before the first component is ever installed.
HSMs can be leveraged to provide EAL 4/FIPS 140-2 level 3 protection of your PKI. Bintel is very experienced with architect and deploying Safenet and Thales HSMs and can even provide your organization with assistance in selecting and acquiring the HSMs.
CLUSTERED SOLUTIONS
The integrity and availability of your PKI environment can have a dramatic effect on the security of your enterprise. Components like Certification Authorities (CA), OCSP and CRL distribution points need to be available around the clock. Installing a second CA will do very little to provide fault-tolerance in most environments.
Clustered solutions will ensure your PKI components are available when your computers need them. Allowing a CA to go offline could prevent clients from enrolling and renewing certificates. It could also result in expired CRL files which will cause clients to stop being able to use certificates. OCSP and CES/CEP servers also have the potential to impact your environment if not carefully designed and deployed in a fault-tolerant solutions.
We can work with you to scale your recovery needs from simple software changes for recover ability, designing virtual machine recovery options (Ou custom built virtualization) for your PKI needs.
HARDWARE SECURITY MODULES (HSM)
Hardware Security Modules (HSM) are available from a number of manufacturers and are leveraged in a PKI to enforce defined procedures. HSMs can be used to ensure no one person can compromise a PKI. They can also be used to speed up signing/issuance in high-volume environments. HSMs can also be used to secure your CAs against the extraction and misuse of your CA private keys.
The proper selection, architecture and implementation of one or more HSMs in your environment is critical. Does your environment require a collusion requirement? If so, a K of N implementation on the HSM is recommended. Do you need to ensure a chain of custody for non-repudiation? Then the design and day-to-day history of the PKI needs to be carefully tracked and audit. This must be in place before the first component is ever installed.
HSMs can be leveraged to provide EAL 4/FIPS 140-2 level 3 protection of your PKI. EGN is very experienced with architect and deploying Safenet and Thales HSMs and can even provide your organization with assistance in selecting and acquiring the HSMs.
CERTIFICATE PRACTICES (CP) AND CERTIFICATE PRACTICE STATEMENTS (CPS)
Certificate Practices (CP) and Certificate Practice Statements (CPS) are some of the most misunderstood PKI related documents in an enterprise. Do you need one? Why would I need one? What should go into a CPS and how does it influence my PKI design? These are all questions that EGN can provide you expertise with. We can work with you to determine your needs and applicability. Where appropriate, we will work with your legal organization to help craft the proper CP and CPS for your enterprise needs.
POLICIES AND PROCEDURES
Time and time again, we see enterprise customers that have an undefined set of practices and procedures for their PKI and Identity systems. EGN can help create the documents and procedures you need to properly manage your identity solution.
PKI BEST PRACTICE ASSESSMENTS
Already have a PKI deployed in your environment or about to put one into production? Is it configured properly? Are all the components (CAs, OCSP, CDP/AIA, Policies, CP/CPS) healthy and up to industry standards? Many organizations don’t know. Why risk your environment due to a problem that could be remediated now? Our Best Practice Assessment compares your environment to industry best practices. You will know your areas of strength and areas that need remediation.
Whether you deployed the PKI or you engaged another company, the PKI Best Practice Assessment can provide you with the knowledge and assurance that it was done right. PKI environments are notorious for hiding problems until it’s too late and the solution is placed into production.
THE PKI BEST PRACTICE ASSESSMENT IS DONE HERE
- CA Operations
- OCSP Servers
- Certificate Enrollment Policy Services (CEP)/Certificate Enrollment Services (CES)
- Cross Forest Enrollment
- PKI Design
- Disaster Recovery
- Documentation
- Certificate Templates
- Physical/Logical Security
- Security and Auditing
- CP/CPS Compliance Audit (if applicable)
DOCUMENTATION SERVICES INCLUDE:
- Data and Key Recovery Procedures
- Certification Authority Management
- Role Separation
- Chain of Custody and Key Ceremonies
- Deployment and Operations Guides
- Disaster Recovery
- Requirements Definition and Business Need Assessments
- Test Use Scenarios and Change Control
- Internal Training Materials